Tag: Privacy
-
The Current State of Platform, Software and Device Security
The year 2012 and the better part of 2013 have witnessed the birth of new computing platforms, social network platforms and general computing trends that not only make the gadget and internet a better place, but also a more dangerous one. These innovations and developed habits expose us to a variety of threats that we…
-
Your internet activities aren’t as safe as you thought
The idea of snooping on undersea cables is not alien in the world of counter-intelligence. In fact, it was in use by the US against the Soviet Union as early as 1970s. Even though such an escapade in the early 70s would only yield specific information, tapping into the current undersea fiber optic cables gives…
-
Government cell phone monitoring shouldn’t come as a surprise
In a recent announcement, it was shown that the National Security Association (NSA) has been “secretly” obtaining private information via Verizon Wireless. With permission through something known as “the blanket order,” Verizon has been handing over a variety of call-related data, such as call lengths, locations, and other unique identifiers. As of yet, it’s stated…
-
How to stay secure on public Wi-Fi
Credit card numbers? Check. Website logins? Check. “Private” chats between cheating spouses? Double check. Spend ten minutes in a coffee shop snooping on the “Free Public Wi-Fi!” and you’ll see all these things and more. Airports, libraries, parks? Same situation. Hotels are a little different, though. All the bandwidth is being taken up by people…
-
5 ways to fight spam in your iCloud email account
I have been an iCloud email user for a while, even before “iCloud” existed (iCloud is Apple’s online email service and other online tools). I was originally a MobileMe and .mac user. Until recently, my iCloud email addresses were relatively free from spam. However, for the past few weeks I have been getting five to…
-
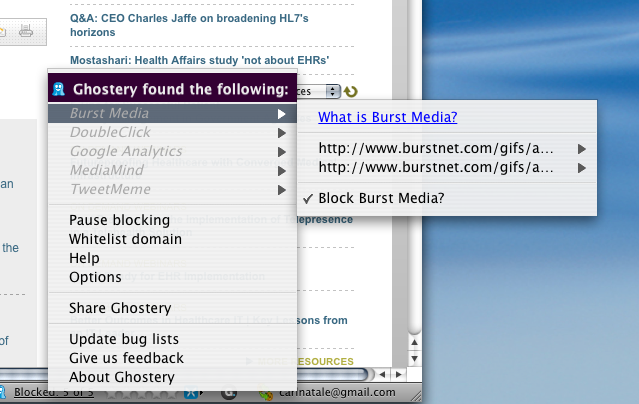
Privacy: Ghostery helps you elude online trackers in all browsers
Browser cookies are the black helicopters of the Internet age. Everyone seems to believe they’re only used for a secret, evil purpose. I guess it depends on your definition of evil. Companies use cookies to store information about Internet users. That information is coupled with other data collected via “tags, web bugs, pixels and beacons…
-
How to download a full backup copy of Wikipedia
I’ve spent plenty of time making jokes about what would happen if Wikipedia went offline in our modern, internet-dependent world – planes dropping out of the sky, no knowledge of any events before 2007, dogs walking their owners – but in all seriousness, any Wikipedia outage will affect millions of students, educators, scientists, and everyday…
-

How I Circumvented Network Authentication (And Got Caught in the Process)
While I’ve never personally worked in the IT field, I have a number of friends who have, and I can appreciate their efforts to keep a network secure and functioning well. Sometimes, though, the cost of network security can be pretty annoying. The university where I work is home to a top-notch group of IT…
-
3 Secure Ways to Store Your Passwords
If you’re anything like me, you probably have all your passwords jammed into a text file or stored in your browser somewhere for easy retrieval when you need them. While convenient, you may want to consider more secure ways to store your passwords to prevent your account(s) from being hacked. The following applications and services…
